- Enterprise
- Enterprise Plus
Connecting Zendesk to Defender for Cloud Apps with a Zendesk user that is not an admin will result in a connection error.
Configure Zendesk
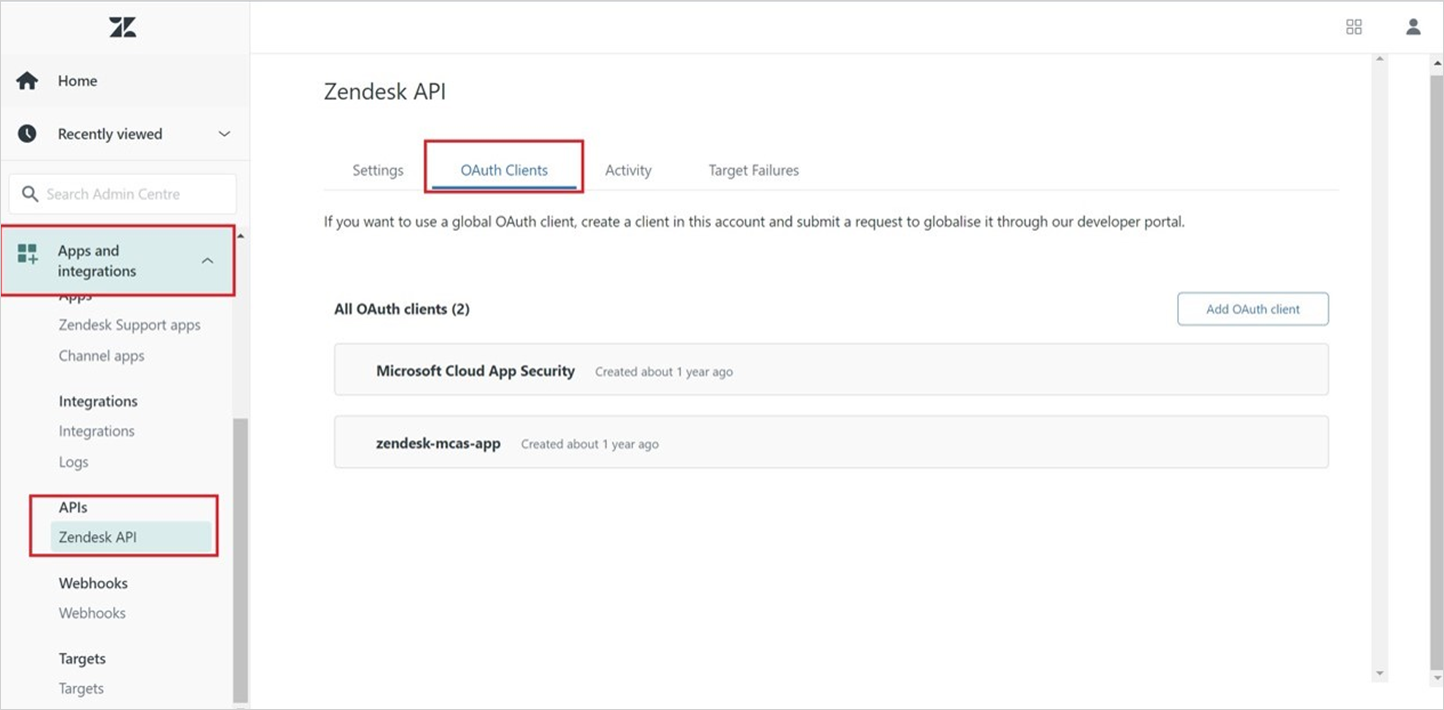
- Navigate to Admin ->Apps and integrations ->APIs ->Zendesk API ->OAuth Client and select Add OAuth client.
- Select New Credential.
- Fill out the following fields:
- Client name: Microsoft Defender for Cloud Apps (you can also choose another name).
- Description: Microsoft Defender for Cloud Apps API Connector (you can also choose another description).
- Company: Microsoft Defender for Cloud Apps (you can also choose another company).
- Unique identifier: microsoft_cloud_app_security (you can also choose another unique identifier).
- Redirect URL: https://portal.cloudappsecurity.com/api/oauth/saga
- For US Government GCC customers, enter the following value: https://portal.cloudappsecuritygov.com/api/oauth/saga
- For US Government GCC High customers, enter the following value: https://portal.cloudappsecurity.us/api/oauth/saga
Configure Defender for Cloud Apps
The Zendesk user that is configuring the integration must always remain a Zendesk admin, even after the connector is installed.
- In the Microsoft Defender Portal, select Settings. Then choose Cloud Apps. Under Connected apps, select App Connectors.
- In the App connectors page, select +Connect an app, followed by Zendesk.
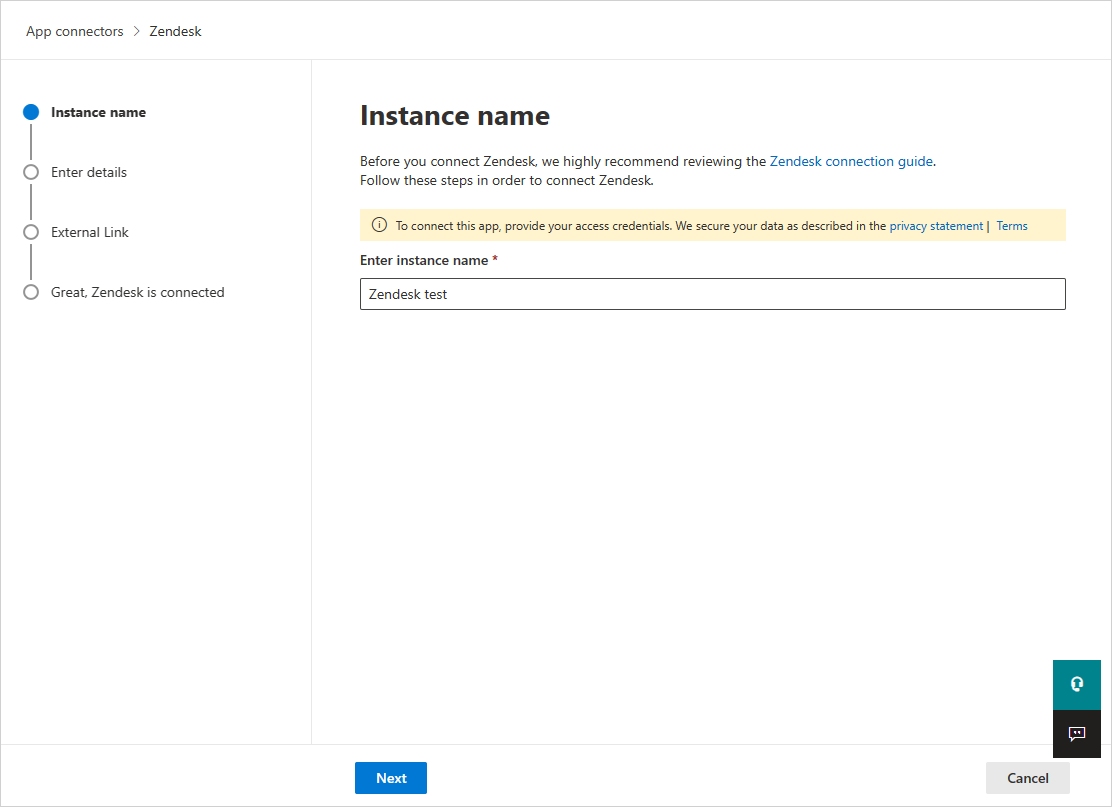
- In the next window, give the connector a descriptive name, and select Next.
- In the Enter details page, enter the following fields and then select Next.
- Client ID: the Unique identifier you used when you created the OAuth app in the Zendesk admin portal.
- Client Secret: your saved secret.
- Client endpoint: Zendesk URL. It should be .zendesk.com .
- In the External link page, select Connect Zendesk.
- In the Microsoft Defender Portal, select Settings. Then choose Cloud Apps. Under Connected apps, select App Connectors. Make sure the status of the connected App Connector is Connected.
- The first connection can take up to four hours to get all users and their activities in the seven days before the connection.
- After the connector's Status is marked as Connected, the connector is live and works.
Microsoft recommends using a short lived access token. Zendesk doesn't currently support short lived tokens. We recommend our customers refresh the token every 6 months as a security best practice. To refresh the access token, revoke the old token by following Revoke Token. Once the old token is revoked, create a new secret and reconnect the Zendesk connector as documented above.
System activities will be shown with the Zendesk account name.
Rate limits
The default rate limit is 200 requests per minute. To increase the rate limit, open a support ticket.
The maximum rate limit for every subscription is described here.
Next steps
If you run into any problems, we're here to help. To get assistance or support for your product issue, please open a support ticket.